BLUETOOTH-PAN
Posted by onlineusman at 7:45 AM

A Bluetooth PAN is also called a piconet, and is composed of up to 8 active devices in a master-slave relationship. The first Bluetooth device in the piconet is the master, and all other devices are slaves that communicate with the master. A piconet typically has a range of 10 meters, although ranges of up to 100 meters can be reached under ideal circumstances.
SECURITY THREAT AND REQUIREMENTS OF WIRELESS PAN
 nizations must not only address the security threats associated with Bluetooth before they implement the technologies; they must also measure the vulnerabilities of the devices they allow to participate in the Bluetooth networks. Specifically, agencies need to address security concerns for confidentiality, data integrity, and network availability. Moreover, since Bluetooth devices are more likely to be managed by users that are less security conscious than administrators, they are more likely to contribute to uncontrolled security drifts. This subsection will briefly cover some of the risks to security, i.e., attacks on confidentiality, integrity, and network availability.
nizations must not only address the security threats associated with Bluetooth before they implement the technologies; they must also measure the vulnerabilities of the devices they allow to participate in the Bluetooth networks. Specifically, agencies need to address security concerns for confidentiality, data integrity, and network availability. Moreover, since Bluetooth devices are more likely to be managed by users that are less security conscious than administrators, they are more likely to contribute to uncontrolled security drifts. This subsection will briefly cover some of the risks to security, i.e., attacks on confidentiality, integrity, and network availability.Loss Of Confidentiality
Loss Of Integrity
Loss Of Avaiability
SOLUTIONS & SECURITY MEASURES FOR WPAN
Management Solutions.
Operational Solutions
Technical Solutions
Labels: BLUETOOTH-PAN 0 comments
WI-FI PRODUCTS
Posted by onlineusman at 7:14 AM
There are several products available now which enable to connect to Wi-Fi Networks around the area. Earlier when Wi-Fi was first started commercially, there were not many devices came built with Wi-Fi network card (Wireless card) which connects to Wi-Fi network. But now almost every handset device on mobile comes with Wi-Fi, Laptops comes with built in Wireless connectivity , desktop computers comes along with Wireless connectivity. Following are few products which provide connectivity to Hotspots.
Desktop Wireless Wi-Fi Cards
 Desktop wireless Wi-Fi cards enable desktop computers to connect to Wi-Fi network available in the area. Wi-Fi network provides height speed internet if available and can share files with in the clients in the network. This kind of network is mostly used in Colleges and Universities, libraries etc. Wi-Fi desktop cards are mostly plugged in Mother board on PCI slot. Some mother board comes with built in Wi-Fi connectivity
Desktop wireless Wi-Fi cards enable desktop computers to connect to Wi-Fi network available in the area. Wi-Fi network provides height speed internet if available and can share files with in the clients in the network. This kind of network is mostly used in Colleges and Universities, libraries etc. Wi-Fi desktop cards are mostly plugged in Mother board on PCI slot. Some mother board comes with built in Wi-Fi connectivityLaptop / Notebook Wireless Wi-Fi Cards

Wi-Fi cards uses in laptops / notebooks to connect to wireless internet around through Wi-Fi network. Most laptops now comes with built in Wi-Fi enable feature. Old model laptops which do not come along with built in Wi-Fi wireless card can plug in Wi-Fi PCMCI slot card to connect to hotspot
Wireless Wi-Fi Routers

Wireless Wi-Fi routers is used to connect clients( having Wi-Fi cards ) with server. Wi-Fi router is attached to server and configure with IP address or in some cases just with internet connection. Now this IP helps connect clients to the server for High speed internet and file sharing with server and other clients. Routers are mostly used when server is expected to handle multiple clients at given time.
Labels: WI-FI PRODUCTS 0 comments
WI-FI SECURITY
Posted by onlineusman at 7:00 AM
 Wi-Fi Security
Wi-Fi SecurityWi-Fi Security feature protects your network and gets quick access associated with Win2K, XP. It supports WEP or WPA and gives you real-time interloper alerts you from free blockers and you feel glad when there is no spyware and no adware in your network to spoil your files. Any users get access to the Internet by means of laptop, handhold games, smart cell phones and PDA. The most important thing is it tenders a trouble-free and cheap method to safe and sound your network connection at any hotspot all over the world. Wi-Fi Security examines data and perceives entrance point in real time and identifies the user who wants to spoil your files.
When we talk about Wi-Fi Security then a detail list come in view to make our network more secure. Wi-Fi discover different security tools such as Airsnort pull through encryption keys when adequate packets have been collected. Airfart sense wireless devices and count their signal powers and make it easy for user to understand, AP Radar used to manage the configuration, Boingo Software helpful for you to include thousand of location all over the world. DStumbler offer a complete set for auditing, KisMAC one of
 the best security weapons, iStumbler used to analyze your dashboard, MacStumbler display information about nearby network, MiniStumbler offering convenience, Wireless Mon allows users to check the position of wireless and so on.
the best security weapons, iStumbler used to analyze your dashboard, MacStumbler display information about nearby network, MiniStumbler offering convenience, Wireless Mon allows users to check the position of wireless and so on.Wi-Fi Security Raw Packet confines tools consist of Air cap facilitate troubleshooting tools such as Wire shark to provide information about protocols and radio signals, eternal offers active and passive analysis of many protocols, libpcap allow link-layer in Windows environments and it contains driver used to extend the OS. The Wi-Fi interference recognition and preclusion Systems is the most powerful wireless instruction system and provide complete security against policy compliance and threats such as Airtight Networks Spectra Guard Enterprise and Sentry which not only detect the threat also remove and delete it from your system, Manage engine Wi-Fi manage the security tools and check that all’s are working or not. It is a big solution of WLAN and Wireless Solutions from Wild Packets, it has a unique gift to address wireless network.
The Analyzers of WiFi Security execute a real-time photograph of all WLAN communications and actions these tools always in action to recognize your data and analysis. There is a long list of analyzers such as Javvin Network Packet analyzer ensure the network performance and prevent the network security, Network Chemistry Packetyzer serve the net with Ethereal packet detain and analysis library, NetScout Sniffer Portable venture network relations. The network instruments observer, tamosoft commview for Wi-Fi and wireshark such a great tool to manage and monitor your network security.
Wi-Fi Security for end clients offer a complete control over the entire network from design to development and including AirMagnet StreetWISE offer automatically diagnose, AirPatrol AirSafe will turn off your network if sense any one interrupt in it, AirTight SpectraGuard S
 AFEdetect classically and make a solution, AirDefense Personal defend the system from the risks that could depiction confidential data and secret dealings and same as AirDefense Personal, Aruba Networks Endpoint Compliance, HotSpotDK, Sana Primary Response Air Cover, and ZENworks USB/Wireless Security provide you a safeguard for your data and transaction. The WiFi networks, robotically sense the necessary WiFi security settings, and caution you about insecure or treacherous networks. keep in mind the following things to make you network secure, don’t put on air your SSID, always enable WPA encryption as an alternative of WEP, Utilize MAC filtering for entrance power and immobilize remote administration.
AFEdetect classically and make a solution, AirDefense Personal defend the system from the risks that could depiction confidential data and secret dealings and same as AirDefense Personal, Aruba Networks Endpoint Compliance, HotSpotDK, Sana Primary Response Air Cover, and ZENworks USB/Wireless Security provide you a safeguard for your data and transaction. The WiFi networks, robotically sense the necessary WiFi security settings, and caution you about insecure or treacherous networks. keep in mind the following things to make you network secure, don’t put on air your SSID, always enable WPA encryption as an alternative of WEP, Utilize MAC filtering for entrance power and immobilize remote administration.Labels: WI-FI SECURITY 0 comments
WI-FI TECHNOLOGY
Posted by onlineusman at 6:51 AM
 WI-FI
WI-FIWireless Fidelity – popularly known as Wi-Fi, developed on IEEE 802.11 standards, is the recent technology advancement in wireless communication. As the name indicates, WI-FI provides wireless access to applications and data across a radio network. WI-FI sets up numerous ways to build up a connection between the transmitter and the receiver such as DSSS, FHSS, IR – Infrared and OFDM. The development on WI-FI technology began in 1997 when the Institute of Electrical and Electronic Engineers (IEEE) introduced the 802.11 technology that carried higher capacities of data across the network. This greatly interested some of major brands across the globe such as the world famous Cisco Systems or 3COM. Initially, the price of Wi-Fi was very high but around in 2002, the IT market witnessed the arrival of a break through product that worked under the new 802.11 g standards. In 2003, IEEE sanctioned the standard and the world saw the creation of affordable Wi-Fi for the masses.

Wi-Fi provides its users with the liberty of connecting to the Internet from any place such as their home, office or a public place without the hassles of plugging in the wires. Wi-Fi is quicker than the conventional modem for accessing information over a large network. With the help of different amplifiers, the users can easily change their location without disruption in their network access. Wi-Fi devices are compliant with each other to grant efficient access of information to the user. Wi-Fi location where the users can connect to the wireless network is called a Wi-Fi hotspot. Through the Wi-Fi hotspot, the users can even enhance their home business as accessing information through Wi-Fi is simple. Accessing a wireless network through a hotspot in some cases is cost-free while in some it may carry additional charges. Many standard Wi-Fi devices such as PCI, miniPCI, USB, Cardbus and PC card, ExpressCard make the Wi-Fi experience convenient and pleasurable for the users. Distance from a wireless network can lessen the signal strength to quite an extent; some devices such as Ermanno Pietrosemoli and EsLaRed of Venezuela Distance are used for amplifying the signal strength of the network. These devices create an embedded system that corresponds with any other node on the Internet.
The market is flooded with various Wi-Fi software tools. Each of these tools is specifically designed for different types of networks, operating systems and usage type. For accessing multiple network platforms, Aircrack-ng is by far the best amongst its counterparts. The preferred Wi-Fi software tools list for Windows users is: KNSGEM II, NetStumbler, OmniPeek, Stumbverter, WiFi Hopper, APTools. Unix users should pick any of the following: Aircrack, Aircrack-ptw, AirSnort, CoWPAtty,Karma . Whereas, Mac users are presented with these options: MacStumble, KisMAC, Kismet. It is imperative for users to pick out a Wi-Fi software tool that is compatible with their computer and its dynamics.
Wi-Fi uses radio networks to transmit data between its users. Such networks are made up of cells that provide coverage across the network. The more the number of cells, the greater and stronger is the coverage on the radio network. The radio technology is a complete package deal as it offers a safe and consistent connectivity. Radio bands such as 2.4GHz and 5GHz depend on wireless hardware such Ethernet protocol and CSMA. Initially, Phase Shift Keying (PSK), a modulation method for conveying data was used, however now it has been replaced with CCK. Wi-Fi uses many spectrums such as FHSS and DSSS. The most popular Wi-Fi technology such as 802.11b operates on the range of 2.40 GHz up to 2.4835 GHz band. This provides a comprehensive platform for operating Bluetooth strategy, cellular phones, and other scientific equipments. While 802.11a technology has the range of 5.725 GHz to 5.850 GHz and provides up to 54 Mbps in speed. 802.11g technology is even better as it covers three non-overlapping channels and allows PBCC. 802.11e technology takes a fair lead by providing excellent streaming quality of video, audio, voice channels etc.
To connect to a Wi-Fi network an adapter card is essential. Additional knowledge about the SSID, infrastructure, and data encryption is also required. The Wi-Fi users don’t have to be concerned with the security issues. The security methods such as MAC ID filtering, Static IP addressing and WEP encryption ensure the user privacy to the maximum.
Labels: WI-FI TECHNOLOGHY 0 comments
3G
Posted by onlineusman at 2:37 AM


 tions-2000 (IMT-2000)', better known as 3G or 3rd Generation, is a family of standards for mobile telecommunications defined by the International Telecommunication Union,[1] which includes GSM EDGE, UMTS, and CDMA2000 as well as DECT and WiMAX. Services include wide-area wireless voice telephone, video calls, and wireless data, all in a mobile environment. Compared to 2G and 2.5G services, 3G allows simultaneous use of speech and data services and higher data rates (up to 14.0 Mbit/s on the downlink and 5.8 Mbit/s uplink ).
tions-2000 (IMT-2000)', better known as 3G or 3rd Generation, is a family of standards for mobile telecommunications defined by the International Telecommunication Union,[1] which includes GSM EDGE, UMTS, and CDMA2000 as well as DECT and WiMAX. Services include wide-area wireless voice telephone, video calls, and wireless data, all in a mobile environment. Compared to 2G and 2.5G services, 3G allows simultaneous use of speech and data services and higher data rates (up to 14.0 Mbit/s on the downlink and 5.8 Mbit/s uplink ).==Overview==! bandwidth of data ! pre-4G ! width="3%" duplex ! width="3%" channel ! description ! geographical areas - - ! TDMA Single‑Carrier (IMT‑SC) colspan="2" EDGE (UWT-136) EDGE Evolution none rowspan="3" FDD TDMA evolutionary upgrade to GSM/GPRS[nb 1] worldwide, except Japan and South Korea - ! CDMA Multi‑Carrier (IMT‑MC) colspan="2" CDMA2000 EV-DO UMB[nb 2] rowspan="4" CDMA evolutionary upgrade to cdmaOne (IS-95) Americas, Asia, some others - ! CDMA Direct Spread (IMT‑DS) rowspan="3" UMTS[nb 3] W-CDMA[nb 4] rowspan="3" HSPA rowspan="3" LTE rowspan="3" family of revolutionary standards. worldwide - ! rowspan="2" CDMA TDD (IMT‑TC) TD‑CDMA[nb 5] rowspan="4" TDD Europe - TD‑SCDMA[nb 6] China - ! FDMA/TDMA (IMT‑FT) colspan="2" DECT colspan="2" none FDMA/TDMA short-range; standard for cordless phones Europe, USA - ! IP‑OFDMA colspan="2" colspan="2" WiMAX (IEEE 802.16) OFDMA late addition worldwide }
Labels: 3G, iPhone, Router 0 comments
ATM
Posted by onlineusman at 2:15 AM
Unlike most connectionless networking protocols, ATM is a deterministic networking system — it provides predictable, guaranteed quality of service. From end to end, every component in an ATM network provides a high level of control. ATM technology includes:
Scalable performance. ATM can send data across a network quickly and accurately, regardless of the size of the network. ATM works well on both very low and very high-speed media.Flexible, guaranteed Quality of Service (QoS). ATM allows the accuracy and speed of data transfer to be specified by the client. This feature distinguishes ATM from other high-speed LAN technologies such as gigabit Ethernet.
Unobstructed speed.
Integration of different traffic types. ATM supports integration of voice, video, and data services on a single network. ATM over Asymmetric Digital Sub
 scriber Line (ADSL) enables residential access to these services.
scriber Line (ADSL) enables residential access to these services.Traditional LAN technologies do not guarantee that data arrives on time or in the proper order. While Ethernet and Token Ring can detect errors, they provide no service guarantees and are not responsible for the recovery of missing or corrupted data packets.
Because a traditional LAN is connectionless, it cannot provide mechanisms that can guarantee successful transmission. For example, it cannot determine the status of the destination adapter to ensure that it can receive a frame. It cannot ensure that bandwidth is available throughout the transmission. Unanticipated blockage, due to the media access control scheme of shared access technologies, can hinder a traditional LAN technology from supporting time-sensitive applications such as video or voice traffic. Traditional LANs can use upper-level protocol drivers to verify packet transmission (retransmitting, if necessary), partition big messages into smaller ones, and use time stamps for synchronization. However, these services add time to the transmission, and none of them provides end-to-end QoS guarantees.
Traditional Internetworking
Like an Ethernet data transfer, a routed data transfer cannot offer guarantees because bandwidth is never reserved ahead of time. The packets being sent over TCP/IP are simply transmitted on the wire and routed. While this allows flexibility in routing around obstructions, network performance can vary a great deal depending on conditions at the routers and on the amount of network traffic.
ATM Networks
While establishing the connection, the ATM endpoint also negotiates a QoS contract for the virtual channel. The QoS contract spells out the bandwidth, maximum transit delay, acceptable variance in the transit delay, and so forth, that the VC provides, and this contract extends from one endpoint to the other through all of the intermediate ATM switches.
The following figure, “ATM Virtual Channel and Packet Transmission,” illustrates
ATM virtual channel and packet transmission.
Unlike Ethernet networks, ATM has no inherent speed limit, and its efficiency is not affected by the distance that the data has to travel. In addition, ATM establishes the pathway for a particular series of packets at the outset and ATM switches make minimal switching decisions thereafter. To travel across the ATM network, data is segmented into same-size cells, and encapsulated with a header that contains information about switching, congestion, and error-checking.
Cells are transmitted in order, and the ATM network uses Virtual Path Identifier and Virtual Channel Identifier (VPI/VCI) numbers in the ATM header to forward them efficiently. A switch reads the header, compares the VPI/VCI to its switching table to determine the correct output port and new VPI/VCI, and then forwards the cell. All the addressing information that the ATM switch needs is contained in the header and is always found in the same place. This makes the forwarding task simple to implement in hardware by, reducing latency. Moreover, with ATM from end to end, there is no data translation required if a packet must travel from a LAN through a WAN to reach a destination LAN. The following figure, “ATM Fixed-Length Cells,” shows two ATM end stations sending fixed-length cells from A to B (although ATM traffic is bi-directional).
ATM places fixed-length cells on the media when the data is produced according to the parameters of a negotiated connection. ATM can simultaneously handle the needs of isochronous (time-dependent) traffic, such as voice and video, and non-isochronous traffic, such as LAN data.
Labels: ATM 0 comments
STORAGE
Posted by onlineusman at 2:11 AM

In contemporary usage, memory usually refers to a form of semiconductor storage known as random-access memory (RAM) and sometimes other forms of fast but temporary storage. Similarly, storage today more commonly refers to mass storage — optical discs, forms of magnetic storage like hard disk drives, and other types slower than RAM, but of a more permanent nature. Historically, memory and storage were respectively called main memory and secondary storage. The terms internal memory and external memory are also used.
The contemporary distinctions are helpful, because they are also fundamental to the architecture of computers in general. The distinctions also reflect an important and significant technical difference between memory and mass storage devices, which has been blurred by the historical usage of the term storage. Nevertheless, this article uses the traditional nomenclature.
Labels: STORAGE 0 comments
VOIP
Posted by onlineusman at 12:03 AM

Internet telephony refers to communications services — voice, facsimile, and/or voice-messaging applications — that are transported via the Internet, rather than the public switched telephone network (PSTN). The basic steps involved in originating an Internet telephone call are conversion of the analog voice signal to digital format and compression/translation of the signal into Internet protocol (IP) packets for transmission over the Internet; the process is reversed at the receiving end.[1]
VoIP systems employ session control protocols to control the set-up and tear-down of calls as well as audio codecs which encode speech allowing transmission over an IP network as digital audio via an audio stream. Codec use is varied between different implementations of VoIP (and often a range of codecs are used); some implementations rely on narrowband and compressed speech, while others support high fidelity stereo codecs.
Labels: VOIP 0 comments
TRANSCEVIERS
Posted by onlineusman at 7:53 PM
 A transceiver is a device that has both a transmitter and a receiver which are combined and share common circuitry or a single housing. If no circuitry is common between transmit and receive functions, the device is a transmitter-receiver. The term originated in the early 1920s. Technically, transceivers must combine a significant amount of the transmitter and receiver handling circuitry. Similar devices include transponders, transverters, and repeaters.
A transceiver is a device that has both a transmitter and a receiver which are combined and share common circuitry or a single housing. If no circuitry is common between transmit and receive functions, the device is a transmitter-receiver. The term originated in the early 1920s. Technically, transceivers must combine a significant amount of the transmitter and receiver handling circuitry. Similar devices include transponders, transverters, and repeaters.Content
1 Radio technology
2 Telephony
3 Ethernet
4 See also
5 References
6 External articles
Radio technology
Two-way radio
A modern HF transceiver with spectrum analyzer and DSP capabilities
In radio terminology, a transceiver means a unit which contains both a receiver and a transmitter. It was quite common to have these units separated. Ham radio operators can build their own equipment and it is always easier to design and build a simple unit having one of the functions, transmitting or receiving. Almost every modern amateur radio equipment is now a transceiver but there is an active market for pure radio receivers, mainly for Shortwave listening operators. An example of a transceiver would be a walkie-talkie, or a CB radio.
Telephony
On a wired telephone, the handset contains the transmitter and receiver for the audio and in the 20th century was usually wired to the base unit by Tinsel wire. The whole unit is colloquially referred to as a "receiver." On a mobile telephone or other radiotelephone, the entire unit is a transceiver, for both audio and radio.
A cordless telephone uses an audio and radio transceiver for the handset, and a radio transceiver for the base station. If a speakerphone is included in a wired telephone base or in a cordless base station, the base also becomes an audio transceiver in addition to the handset.
A modem is similar to a transceiver, in that it sends and receives a signal, but a modem uses modulation and demodulation. It modulates a signal being transmitted and demodulates a signal being received.
Ethernet
100BASE-TX to 100BASE-FX transceiver.
Transceivers are called Medium Attachment Units (MAUs) in IEEE 802.3 documents, which were widely used in 10base2 and 10base5 Ethernet networks. Fibre-optic gigabit and 10 gigabit Ethernet utilize transceivers known as GBIC, SFP, XFP, and XAUI.
Labels: TRANSCEVIERS 0 comments
TELECOMMUNICATION NETWORKING
Posted by onlineusman at 10:55 AM

The main function of any telecommunications network is to provide efficient transmission of information from a point of origin to a point of termination. A telephone call is the easiest way to understand the function. A call is initiated at a given point, with the signal routed through a series of nodes that may involve a combination of wired switches, Internet relays, and wireless nodes. The signal eventually terminates at a local switch, where is it then routed to the equipment used by the intended recipient. This process takes place within seconds, and establishes a connection that allows the parties to interact in a real-time fashion.
Today, there are several basic types of telecommunications networks in use. Along with the PSTA, or public switched telephone network, that most people are familiar with, there is also the Internet, a medium that is increasingly used for both voice and visual communications. Private computer networks are a common tool in many businesses today, as well as many institutions of higher learning. These basic types are all classified into several categories, which include such options as wide area networks, local area networks, and virtual private networks.
COMPUTER NETWORKING
Posted by onlineusman at 2:48 AM

A computer network, often simply referred to as a network, is a collection of computers and devices connected by communications channels that facilitates communications among users and allows users to share resources with other users. Networks may be classified according to a wide variety of characteristics. This article provides a general overview of types and categories and also presents the basic components of a network.
Labels: COMPUTER NETWORKING 0 comments
WIRELESS NETWORKING
Posted by onlineusman at 2:40 AM
 WIRELESS NETWORKING
WIRELESS NETWORKINGWireless computer networking means that the communication between computers without the clustered wires. It is ideal for the situations where the cabling is not possible. There are different types of wireless network such as WLAN (which is based on the IEEE 802.11b standard), Wi-Fi, Wi-Max, GSM, Bluetooth and Infrared etc. The signals are usually transmitted through radio and electromagnetic waves. The hardware devices that are used in a wireless network are routers, switches, access point, wireless LAN cards, adapters, antennas, bridges, PCMCIA cards, WLAN access, station adapters and wireless modems.
Wireless network offers the flexibility, mobility, scalability to work everywhere within the range of your network. WLANs can be configured in a variety of ways to meet the needs of specific applications.
Labels: WIRELESS NETWORKING 0 comments
NETWORK PROTOCOLS
Posted by onlineusman at 2:39 AM
In networking, the communication language used by computer devices is called the protocol. Yet another way to classify computer networks is by the set of protocols they support. Networks often implement multiple protocols to support specific applications. Popular protocols include TCP/IP, the most common protocol found on the Internet and in home networks.

Labels: NETWORK PROTOCOLS 0 comments
NETWORK DESIGN
Posted by onlineusman at 2:38 AM
Computer networks also differ in their design. The two types of high-level network design are called client-server and peer-to-peer. Client-server networks feature centralized server computers that store email, Web pages, files and or applications. On a peer-to-peer network, conversely, all computers tend to support the same functions. Client-server networks are much more common in business and peer-to-peer networks much more common in homes.

A network topology represents its layout or structure from the point of view of data flow. In so-called bus networks, for example, all of the computers share and communicate across one common conduit, whereas in a star network, all data flows through one centralized device. Common types of network topologies include bus, star, ring and mesh.
Labels: NETWORK DESIGN 0 comments
DSL
Posted by onlineusman at 2:38 AM
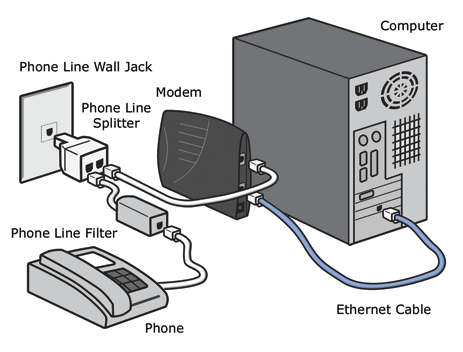
The least expensive type of WAN uses the Internet over a dial-up modem. This type of WAN is not as popular, since the price of DSL has decreased enough to become competitive with dial-up accounts. A dial-up modem only operates at 56 kilobits per second (kbps), while a standard DSL connection is about 20 times faster. A dial-up connection also cannot share telephone service. Finally, dial-up is not an "always on" connection. When offices are in different time zones, this can effectively reduce WAN uptime.
A WAN is an excellent way for companies to utilize geographically remote resources and centralize productivity. A leased line or affordable DSL-based WAN allows employees, field personal, and management full or restricted access to pertinent data twenty-four hours a day, seven days a week. Considering the negligible cost of DSL today, a WAN makes good business sense.
Labels: DSL 0 comments
Wide area networks (WANS)
Posted by onlineusman at 2:36 AM
 Wide area networks (WANS)
Wide area networks (WANS)A Wide Area Network (WAN) is a network that spans a large geographical area, the most common example being the Internet. A WAN is contrasted to smaller local area networks (LANs) and metropolitan area networks (MANs). LANs are home or office networks, while a MAN might encompass a campus or service residents of a city, such as in a citywide wireless or WiFi network.
The Internet is a public WAN, but there are many ways to create a business model or private WAN. A private WAN is essentially two or more LANs connected to each other. For example, a company with offices in Los Angeles, Texas and New York might have a LAN setup at each office. Through leased telephone lines, all three LANs can communicate with each other, forming a WAN.
Routers are used to direct communications between LANs communicating on a WAN. The router, installed on the leased line, reads the "envelopes" or headers on each packet of data that passes through the WAN, sending it to the proper LAN. When the packet arrives at the LAN, a device called a switch sends the data packet on to the correct machine. Hence, the WAN acts like an interface between LANs for long-distance communication. A WAN that runs on a leased line is a private WAN, as there is no public traffic on the line.
Because leased lines are expensive, many businesses that require a WAN use an Internet Service Provider (ISP) to provide WAN access instead. In this case, each LAN in the WAN communicates through a standard digital subscriber line (DSL) account. The DSL Internet account uses an existing telephone line while sharing that line with the telephone.
Labels: WAN, Wide area networks 0 comments
Ethernet
Posted by onlineusman at 2:35 AM

Typically, a suite of application programs can be kept on the LAN server. Users who need an application frequently can download it once and then run it from their local hard disk. Users can order printing and other services as needed through applications run on the LAN server. A user can share files with others at the LAN server; read and write access is maintained by a LAN administrator. A LAN server may also be used as a Web server if safeguards are taken to secure internal applications and data from outside access.
In some situations, a wireless LAN may be preferable to a wired LAN because it is cheaper to install and maintain.
Labels: Ethernet 0 comments
TYPES OF NETWORKING
Posted by onlineusman at 2:33 AM
 TYPES OF NETWORKING
TYPES OF NETWORKINGLocal area networks (LANS)A local area network (LAN) is a group of computers and associated devices that share a common communications line or wireless link. Typically, connected devices share the resources of a single processor or server within a small geographic area (for example, within an office building). Usually, the server has applications and data storage that are shared in common by multiple computer users. A local area network may serve as few as two or three users (for example, in a home network) or as many as thousands of users (for example, in an FDDI network). Major local area network technologies are: Ethernet Token Ring FDDI

Labels: TYPES OF NETWORKING 0 comments


















